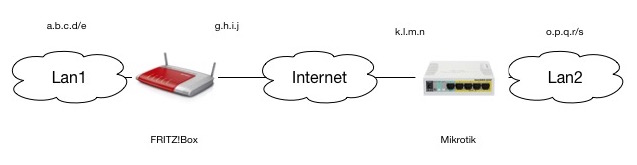
IPSec between a FRITZ!Box and a Mikrotik
FRITZ!box configuration (assuming linking 2 class C networks):vpncfg {
connections {
enabled = yes;
editable = no;
conn_type = conntype_lan;
name = "FritzMikrotik"; // Name of the connection
boxuser_id = 0;
always_renew = yes;
reject_not_encrypted = no;
dont_filter_netbios = yes;
localip = 0.0.0.0;
local_virtualip = 0.0.0.0;
remoteip = k.l.m.n; // Remote IP
remote_virtualip = 0.0.0.0;
keepalive_ip = 0.0.0.0;
localid {
ipaddr = g.h.i.j;
}
remoteid {
ipaddr = k.l.m.n; // Remote IP
}
mode = phase1_mode_idp;
phase1ss = "alt/all/all";
keytype = connkeytype_pre_shared;
key = "SecretPassword"; // Presharedkey
cert_do_server_auth = no;
use_nat_t = no;
use_xauth = no;
use_cfgmode = no;
phase2localid {
ipnet {
ipaddr = a.b.c.d; // Local Subnet
mask = 255.255.255.0;
}
}
phase2remoteid {
ipnet {
ipaddr = o.p.q.r; // Remote Subnet
mask = 255.255.255.0;
}
}
phase2ss = "esp-3des-sha/ah-no/comp-no/pfs";
accesslist = "permit ip any o.p.q.r 255.255.255.0";
}
ike_forward_rules = "udp 0.0.0.0:500 0.0.0.0:500",
"udp 0.0.0.0:4500 0.0.0.0:4500";
}
And for the MikroTik:/ip ipsec proposal
add enc-algorithms=3des name=Fritz pfs-group=none
/ip ipsec peer
add address=g.h.i.j/32 enc-algorithm=3des lifetime=7h local-address=\
k.l.m.n nat-traversal=no secret=SecretPassword
/ip ipsec policy
add dst-address=a.b.c.d/24 proposal=Fritz sa-dst-address=g.h.i.j \
sa-src-address=k.l.m.n src-address=o.p.q.r/24 tunnel=yes
/ip firewall filter
add action=accept chain=input comment=\
"Allow Access to Router Interface from IPSEC trusted Network" \
dst-address=o.p.q.r src-address=a.b.c.d/24
/ip firewall nat
add action=accept chain=srcnat comment="NAT BYPASS for IPSEC Tunnel" \
dst-address=a.b.c.d/24 src-address=o.p.q.r/24
/ip firewall raw
add action=notrack chain=prerouting comment=\
"Fasttrack BYPASS for IPSec traffic " dst-address=o.p.q.r/24 \
src-address=a.b.c.d/24
add action=notrack chain=prerouting dst-address=a.b.c.d/24 src-address=\
o.p.q.r/24
Please note that the NAT bypass rule should be at the top of the NAT list.
Thanks to one of the very helpful engineers at Mikrotik who helped correct an excess policy declaration
